| Windows 2000 / XP Desktop Computer Security - 3 | |
|
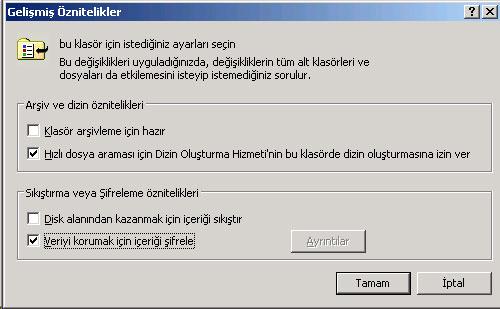
This article covers the last part of Windows operating system security issue. The main topics are as follows: shutting down the unnecessary services, management of user rights, the modifications to be done on registry files, and lastly EFS (Encyripted File System) and SRP (Software Restriction Policies). Services: The following list contains the services that mostly remain unused on desktop computers. Alert: While working through a number of tasks, this service sends message to the computer user about the task concerned. Clipbook: This service enables the sharing of information kept on the "Clipboard" over the network. Computer Browsing Service: This service enables the displaying of the computers on the network and the information they share from network sharing fields. When this service is shut down, the user should not forget the source of the relevant sharing so that he/she could access it later by typing it on the Explorer window. Fax Service: This service enables receiving fax messages. FTP Publishing Service: This is a service included in IIS (Internet Information Server). It is not installed as default. It is not recommended for the desktop computers to share files through an FTP server that ISS uses. ISS Admin Service: This service enables to access ISS services remotely. This service should not be available on desktop computers. Internet Connection Sharing: This service enables the computer that is connected to Internet to run as a network gateway. It is recommended to use real IPs at our campus. Messenger: This service runs together with Alert service. It sends the messages to a many number of computers. NetMeeting Remote Desktop Sharing: This is a service used by system administrators. Routing and Remote Access: This service enables the computers on a network to access to other computers on another network. Or, this service is used on a computer which will be used as remote access server. The desktop computer users do not need this service. Simple Mail Transfer Protocol (SMTP): Desktop computers should not be used as a e-mail servers. This service, which comes along with ISS packet, should be should down or it should be removed completely. Simple Network Management Protocol (SNMP) Service: This protocol enables the administration of network devices remotely. However, this protocol has recently opened many vulnerabilities. Therefore, it should be shut down by users who do not have to use it necessarily. Simple Network Management Protocol (SNMP) Trap: This is a service that must run on the device with which the SNMP sevice will communicate. It is better to shut it down if it is not being used. Telnet: It provides the remote administering on the command line of service network devices that do not operate actively as default on desktop computers. However, it is not recommended since it sends the user code-password pair and other information as plain text. World Wide Web Publishing Service: This is the Microsoft service that is mostly attacked and that has the most vulnerabilities. The service does not run as default so it is not active on the system. It is recommended that the service is removed completely from the desktop computers. It is also recommended that you use more developed servers on computers that are used as servers. What to do on Regedit file: The following values are recommended. For more information related to this topic, you should take a look at SANS Security Baseline documents. EFS (Encrypted File System): Until now, we have talked about the precautions we may take against the possible attacks on the network. In this section, you will find information about how to protect the data on your computer against people that may sit at your computer with malicious intentions. EFS is a characteristic of Windows operating systems and it enables keeping the files as encrypted on the hard disc. The operation of the mechanism is based on the Public key encryption system. Users do not have to own admistrator rights to use it. To encrypt the directories by using EFS, the user can make use of his/her own certificates or the certificates that Windows XP will create at the time she/he wishes to use. The subdirectories of the encrypted directory and the files that will be saved to the encrypted directory will be encrypted with the same key. To encrypt the directory, the user should select "Properties" on the directiory. Then, the user should select "Encrypt the content to protect data" option under Advanced tab.
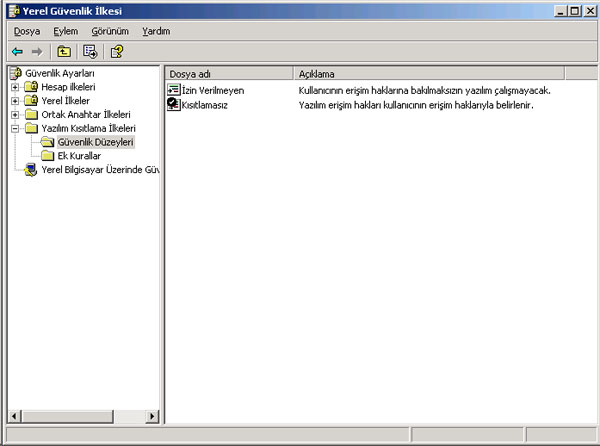
The encrypted directory is only accesible by the user that encrypted it or by the data saving agents to whom the user is a subscriber to by default. Whenever the user profile is distorted, or the password of the user is changed by the administrator, or the user is not available for certain reasons, the encrypted file(s) can be accessed by data saving agents. SRP (Software Restriction Policies): This is one of the Windows XP operating system features that enable the administrator to determine which programs are going to be permitted to operate on a domain or on desktop computer.
SRP rules are accessed in "Local Security Policy". The default value of the policy is "unrestricted" (this feature allows every program to operate). The administrator may change this feature and make it "disallow" (not allowed to operate) according to his/her strategies. With SRP, there are two approaches the administrators may implement to control the operation of programs: 1. Allowing only the secure codes to operate: This method can be implemented when all the secure programs and the the related samaller programs can be specified. That means if an administrator knows all the programs that should run then SRP can be applied to control execution to only this list of trusted applications. In general the method is applied when the computer is configured to served as; For example, an administrator may only allow Internet Exlporer to operate. Then the user will receive a message telling that he/she will not be able to operate any other program, whenever he/she wants to run one. 2. Disallowing undesired applications as needed: This is an approach that should be applied on computers that do not need any restriction where the administrator wants to enforce rules to prevent the use of undesired applications. For example, an administartor may enforce a policy that disallows the use of the file sharing programs. Rules for Identifying Software: 1. Hash rule: a cryptographic fingerprint, which uniquely identifies a software, is used. With a hash rule, software can be renamed or moved into another location on a disk, but it will still match the hash rule defined by the administrator. 2. Path rule: this rule is specified according to the location of the software in the stucturing of directories. When the software is moved to another folder, the rule will be inapplicable. 3. Certificate rule: This rule is specified according to the the certificate of software publisher. The executable file is independent of the directory it is in. 4. Zone rule: A rule can identify software from the Internet zone (local networks, safe sites, banned sites) from which it is downloaded. It is important to remember to check whether smaller programs, which are associated with the program you will specify a rule about, are running relevant tasks together. This is especially important when the administrator allows the user to run only some specific programs. During the testing phase, the tasks that are run together with associated programs are monitored with msinfo.exe program. Then the rules are specified and enforced about the suitable ones. İbrahim ÇALIŞIR |
||
| - TOP - |