
| VPN | |
| Contents |
| The Legislation of 5651: The Law for the Internet |
| Emergency Situation Intervention |
| Foresights on Technology for 2009 |
| VPN |
| WiMAX and WiFi |
| CISN Archive |
| Send Feedback |
|
What is VPN? VPN (Virtual Private Network) is a technology developed with the purpose of ensuring secure communication over the Internet and providing data transfer. The most important reason for VPN to be preferred is the cost. It is the easy and secure use of the infrastructure of an operator, as if it were a private network, for those establishments who do not own a back upped, reliable and fast network that needs high funding. This application, where general communication network systems are used, encompasses the 'tunneling protocol' system between the nodes and the security procedures of 'authentication' and 'encryption'. VPN Solutions: The data is packed and encrypted at one end of the VPN tunnel and unpacked and decrypted at the other end and conveyed securely. Along the tunnel various protocols maintain the transfer. These are IPSec (IP Security) and SSL (Secure Sockets Layer) protocols. 1) IPSec VPN: This protocol provides strong encryption and guarantees data integrity. Various encryption methods are used. The most prevailing of these is the 3-DES (Digital Encryption Standard). For the client to ensure this connection certain software has to be installed on the computer. 2) SSL VPN: It is the protocol that enables connection to the VPN system from any node on the internet backbone using a web browser (Firefox, Safari, Opera etc.). In contrast to IPSec VPN there is no need to install any software. For this feature it is also named as the clientless VPN. VPN Types According to the Usage Purposes: 1) Intranet VPN: These are structures that enable units which are on the same network system to connect to the data centre rapidly, in an encrypted manner and directly. To exemplify, the engineering departments which are on the same campus are able to connect to data base of the engineering faculty. 2) Extranet VPN: It is the structure that enables units on distant campuses to connect over the main internet backbone. There has to be a VPN server at both units (See. Fig.1). Two different establishments residing in different cities accessing to each others data bases within their joint project, can be given as an example. The security must be at highest level for this structure. 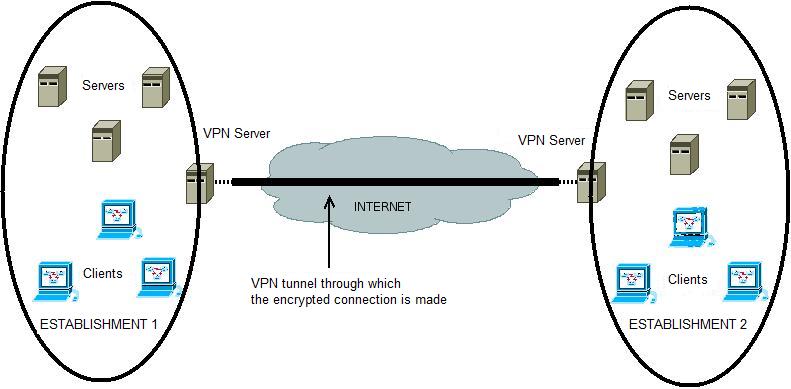 Fig. 1 - With the VPN system provided for two establishments far away from each other, secure data transfer can be provided. 3) Remote Access VPN: It is the structure that enables users to access the data centre from distant points (home, hotel, conference hall etc.). Owing to this structure, the user can connect to the VPN server and virtually become a local user of the network (See Fig. 2). This connection is also done via the main Internet backbone. Therefore, the encryption and authentication structure must be at the highest level. 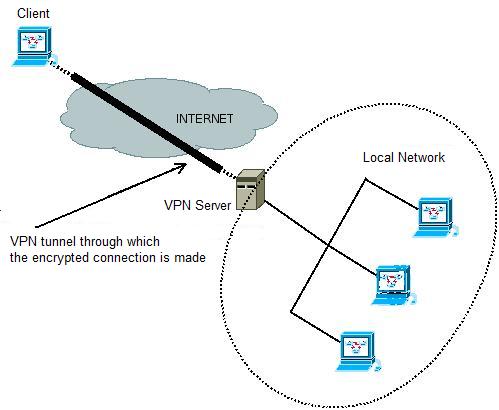 Fig. 2 - The client virtually becomes a Local Network user by VPN connection VPN in METU: VPN technology is being used for trouble shooting problems that might arise in the in-campus networks with the purpose of access from outside campus during out of working hours. Such access is provided by open source coded software (OpenVPN) or network devices with VPN support. That is how problems encountered are solved in the nick of time and the duration the users being affected by downtime are minimized. Resources: http://www.cisco.comhttp://www.freebsd.org http://www.olympos.org http://www.openvpn.org Hüsnü Demir - Saygın Ozan Caner |
||
| - TOP - |