The progressive advance of the information technologies equip the authorized users with the tools that enable him/her to access the veritable information in lesser time. Today, however, as well as providing access, it is equally important to maintain the genuineness, certitude and integrity of the information that is accessed. The information should be protected from threat of incognizant users, malicious attackers, and viruses. So much widespread are the activities that threaten the means to access information as next to the firsthand attacks on information which are started in 2000 by "W32.Nimda" virus.
The great majority of the attacks are against computers that use Windows NT/2000/XP operating systems. The system administrators and users are to implement some specific precautionary measures to maintain the secure and uniterrupted use of the systems.
In this article we will look into two of the 4 main measures that must be taken on computers with Windows NT/2000/XP operating systems. The "Basic Security Settings" topic covers the settings that can be implemented by almost every user on any of the operating systems whereas "Medium Level Security Settings" section covers the settings that can be implemented by Windows NT/2000/XP users or these settings can be implemented by consulting the system admnistrators.
Most of the administrators pay attention only to security concerns at the level of network environment and take measures specifically against them. However, they should not forget that they may experience seriously dangereous attacks in other real environments.
Click "Apply to All Folders" button.
Use password
The user must use a password when establishing local connection to a computer. When installation is completed, many system administrators prefer to use blank password and likewise, when a computer is provided to many users, they prefer to use blank password. If the users leave the password field blank, any person who is capable of accessing the computer physically, can also gain access to all the information available on the system. Moreover, a person with malicious intent, who has gained access to the system over the network, may obtain the user names on the computer and gain user rights to perform applicaitons on the computer. In spite of the fact that network access to computers of those users who use blank password is prohibited on Windows XP Professional operating systems, physical access to the computer still constitutes a serious security vulnerability if the user is not using a password.
Cancel the "Guest" account
"Guest" user account allows access to shared resources on the network without using a password. Windows NT/2000/XP operating systems, except Windows XP Home Edition, allows the user to disable this account.
To change the name of the "Guest" user;
You should double click "Rename Guest Account" under the following path; Control Panel | Administrative Tools | Local Security Settings | Local Policies | Security Options and a name other than "Guest" should be given.
To disable the "Guest" user account;
Right click the "Guest" account under the following path; Control Panel | Administrative Tools | Computer Management | System Tools | Local Users and Groups | Users then select "Properties" in the menu displayed, click the "Account is disabled" option under "General" tab.
Since Windows XP Home Edition does not allow the user to disable "Guest" account, this account should be secured by using a strong password.
Install anti-virus software program
Viruses, which is a perilous concern for most of the users today, exhaust the system resources by way of creating network traffic and sending mass e-mail messages. For nearly every organisation, it is an indispensible security measure to keep updated anti-virus software on desktop computers. Though this is not the only solution for the organisations to ward off viruses, it is the most fundemental measure to take for the users of desktop Windows operating system.
If the user leaves the anti-virus program that he/she installed not updated, it constitutes a security vulnerablity rather than a security measure. If your sole defense against the viruses is placing your trust in your ant-virus software, it is a very high probability in the world of today's Internet that one of the programs you are downloading from Internet contain one of those newly emerged harmful viruses which may infect your system. For this very reason, it is extremely important to keep your virus scanning program up-to-date.
McAfee VirusScan 4.5.1, which is a software licensed to METU campus, can be found at ftp://ftp.cc.metu.edu.tr/Security/McAfee. Users can download the Service Pack files of the virus
scanning software from the same address. The last update files can be found at ftp://ftp.metu.edu.tr/popular/virus-updates/McAfee. Programın insatallation, updating and
general information about viruses can be found at www.antivirus.metu.edu.tr.
Medium-level security settings
Use password protected screen saver
An ignorant person or a person with malicious intent may sit at your computer when you are on a coffee or tea break. This perpson may interrupt the programs that are running on your computer meanwhile or may intentionally try to give harm to your system. To prevent this, a password protected screen saver should be used. (The user must use a well-thought, strong password). Password protected screen saver indicates that the computer is still running; therefore it cannot be shut down unintentionally.
Change "Administrator" account name
Most of the attacks on a computer concentrate on the fact that a user named as "administrator" should have more extended rights than any other user on the computer. If the user account that is to have more extended rights than any other user on the computer is named something else than a name like "administrator" the attack would be unsuccessful since there is no user named as "administrator".
To change this name you should first;
Double click "Rename Administrator Account" under the following path; Control Panel | Administrative Tools | Local Security Settings | Local Policies | Security Options and then, write another name instead of "Administrator".
Then you should right click "Administrator" under the following path; Control Panel | Administrative Tools | Computer Management | System Tools | Local Users and Groups | Users and then, select "Rename" from the menu displayed and wirte another name instead of "Administrator".
Limit the number of user accounts
The presence many user accounts that belong to users who do not use the system resources anymore is a nuisance for the system. To prevent unauthorised use of the acccounts, the computer coordinator should spot the disused accounts and delete or arcihve them as soon as possible.
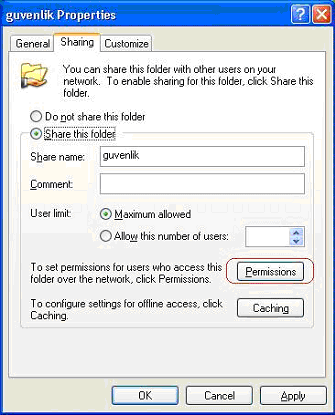
Organize the sharing rights
If a file is shared on Windows NT/2000/XP operating sytems, group "Everyone" is automatically provided with all rights by default. For this reason, once a file is shared, the rights should be reorganised. While performing file sharing, you should click the "Permission" button and remove "Everyone" from among the list of the users that are to access the file. However, the users who have the right to access the local disc, can be included in the list.
Close the Remote Desktop connection
Although Remote Desktop Connection feature provides a flexibility for the administrators to access other computers from their own systems, it is obvious that unless the network security is fully guaranteed in every respect or essential security updates have been completed, it provides a better tool for people with malicious intentions since the vulnerabilities it produces exceeds its benefits.
To make sure that Remote Desktop Connection is disabled;
"Do not allow new client connection" line under the following path Start | Run | gpedit.msc | Computer Configuration | Administrative Templates | Windows Components | Terminal Services should be enabled.
Clean the "Page" file before shutdown
Much of the essential information such as the Administrator Password is kept within the "Page" file during the use of the computer. Users or those people who gained system access illegitimately can obtain that information from this file secretly. The user may evade this hazard by deleting the information available in this file before shutting down the system.
In Windows 2000/XP operating system, if you enable "Clear virtual memory page file" option under the following path; Control Panel | Administrative Tools | Local Security Policy | Security Settings | Local Policies | Security Options, the task will be carried out automatically by the computer before it is shut down.
Disable the default sharings
In Windows 2000/XP operating systems, the partitions of the hard disc are shared secretly as default for the use of the administrators. However, people with malicious intentions may turn this feature into a vulnerability and use it to access your computer easily.
To prevent it happen, do the following in the "regedit" registry file;
The Dword value of "AutoShareWks" line under the following path; HKLM / SYSTEM / CurrentControlSet / LanManServer / Parameters should be changed as "0" and it should be created. After doing that, the computer should be restarted.
Prevent automatic CD running
The best method for people with harmful intent to steal private information and to access private resources is to use programs such as "Trojan Horse" which are executed on CDs that automatically run when the system is restarted.
To overcome this threat;
The Dword value of "AutoRun" line under the following path; HKLM / System / CurrentControlSet / Services / CDRom should be changed as "0" and it should be created.
In the next issue, the topics such as shutting down the unnecessary services, keeping log files, user account settings, security settings, additional security arrangements within the registry file will be covered under "Advanced Security Settings" title and additional features such as EFS (Encyripted File System) and SRP (Software Restriction Policies) will be talked about.
İbrahim Çalışır


